Deepfakes and Cybersecurity: Detecting & Preventing AI-Based Attacks (2025 Guide)

Introduction: When AI Turns Against Us
Artificial intelligence has transformed the way we work, create, and communicate. But the same power that enables innovation is also being weaponized. One of the fastest-growing threats today is deepfake security breaches — where AI-generated videos or voices are used to deceive people and organizations.
In 2024, a major company lost $25 million in a single deepfake video call scam. An employee joined a meeting with what seemed to be his executives — but every face in that call was AI-generated. This wasn’t fiction. It was the moment the world realized that even the sharpest professionals can be fooled when AI is the attacker.
As we move through 2025, protecting against deepfakes has become a core part of cybersecurity strategy. This guide explains how these attacks work, what detection tools are available, and how you can stay one step ahead.
What Exactly Is a Deepfake?
A deepfake is a piece of synthetic media — usually a video, photo, or audio clip — created by artificial intelligence. Using advanced machine-learning models, these systems can mimic a real person’s voice, face, or body movements with astonishing precision.
Deepfakes rely on deep neural networks such as Generative Adversarial Networks (GANs), which learn to recreate human expressions and sounds from training data. The result? Fake videos that can look entirely real to the human eye.
Common uses in cybercrime include:
- Impersonating executives or public figures during live video calls
- Voice cloning to authorize financial transactions
- Fabricating fake news or political statements
- Creating synthetic identities for fraud or blackmail
The danger lies in how easily this technology is now available — anyone with a powerful laptop and free software can make a convincing fake.
The Rise of Deepfake Security Threats
Over the past two years, deepfake security risks have moved from isolated incidents to widespread corporate concern. What used to take specialized skills can now be done in minutes using public AI tools.
The $25 Million Video Scam
In one verified case, criminals used deepfake videos to impersonate a company’s top executives during a video conference. The employee believed he was speaking with his CFO and finance team — all were fake. After following instructions to move funds, the business lost more than 25 million USD before realizing it had been scammed.
This event underscored a harsh reality: traditional cybersecurity tools can’t detect human-level deception. Firewalls and antivirus programs aren’t built to question what appears to be a normal Zoom call.
How Deepfakes Power Modern Attacks
- AI-Phishing: Instead of fake emails, scammers now send personalized videos or audio messages.
- Corporate Fraud: Deepfake impersonation of leaders to trigger urgent wire transfers.
- Reputation Damage: Fake videos spread misinformation about public figures or brands.
- Bypassing Biometrics: Cloned faces or voices can trick weak verification systems.
The combination of realism and social trust makes deepfakes one of the hardest cyber threats to detect.
Tools Leading the Fight Against Deepfakes

🧩 Intel’s FakeCatcher
Intel’s FakeCatcher is one of the most advanced real-time deepfake detection systems available today. Unlike traditional tools that simply analyze pixels, FakeCatcher examines biological signals — subtle blood-flow patterns in real human skin that deepfake models can’t replicate.
With up to 96% accuracy and instant analysis, it’s highly effective for live video verification, media authentication, and fraud prevention in real-time communications.
🔗 Official Source: Intel FakeCatcher – Real-Time Deepfake Detector
🛡 Reality Defender (RD)
Reality Defender is a browser-based and API-driven tool designed to detect manipulated media across video, audio, image, and even text formats. It’s widely used by enterprises, banks, and media outlets to ensure that uploaded files or conference calls aren’t AI-generated.
Their developer SDK allows seamless integration into corporate platforms — ideal for verifying identity documents or preventing payment scams involving AI-generated personas.
🔗 Official Website: Reality Defender
🔍 Microsoft Video Authenticator
Microsoft Video Authenticator analyzes both photos and videos to determine the likelihood that they’ve been digitally altered. It provides a confidence score — a visual gauge showing how real or fake the content is.
This tool was developed as part of Microsoft’s broader disinformation defense initiative and is particularly useful for journalists, law enforcement, and digital platforms handling user-generated content.
🔗 Learn More: Microsoft Video Authenticator
⚙️ Deepware Scanner
Deepware Scanner is a dedicated AI platform that scans uploaded videos and detects synthetic manipulation. It’s fast, web-based, and supports a variety of formats — making it perfect for content creators, investigators, and cybersecurity teams looking to verify viral clips.
🔗 Try It Here: Deepware Scanner
🧰 Hive Moderation AI
Hive Moderation AI combines large-scale content moderation with deepfake detection algorithms. It automatically flags synthetic or manipulated media across social networks, corporate systems, and digital ad platforms.
It’s often used by companies to filter harmful or deceptive AI content before it reaches the public.
🔗 Visit: Hive Moderation AI
🧬 FaceGuard & CLRNet (Research Models)
These research-grade frameworks — FaceGuard and CLRNet — focus on developing innovative techniques such as embedding invisible watermarks into authentic videos and spotting microscopic anomalies in deepfake content.
Although not yet mainstream commercial tools, they represent the future of deepfake forensics in cybersecurity and digital trust.
🔗 Research Paper: FaceGuard on arXiv
Building a Strong Deepfake Defense Strategy
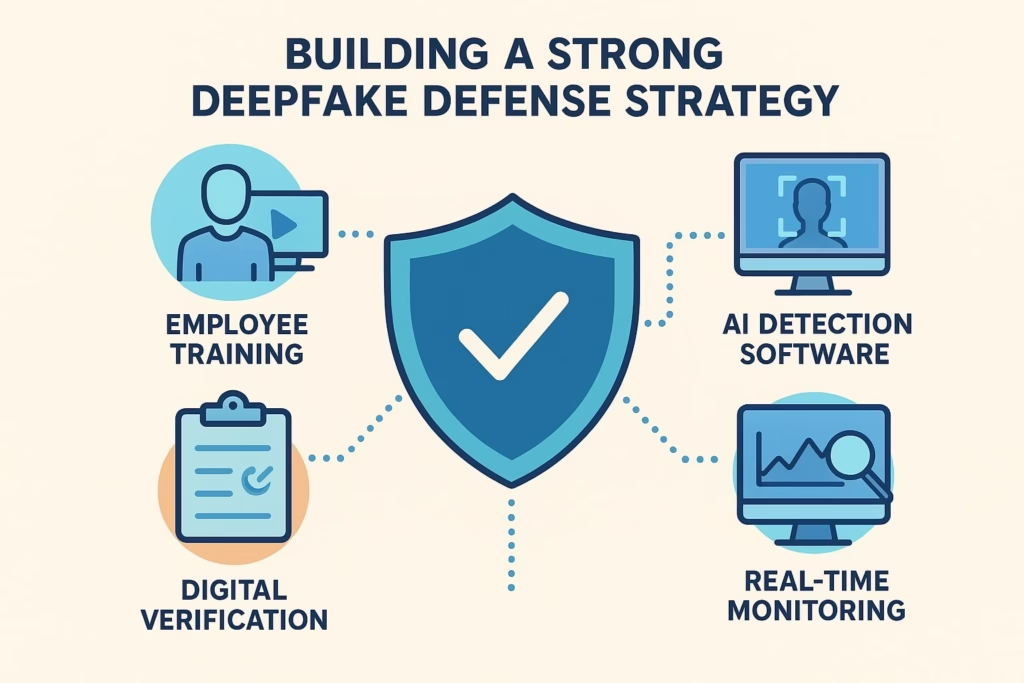
1. Verify Every Channel
Never approve financial or confidential actions based solely on video or voice. Implement multi-factor confirmation, such as a secondary call, digital signature, or secure chat verification.
2. Train Employees to Spot Fakes
Human awareness remains the strongest first line of defense.
Encourage teams to look for these red flags:
- Inconsistent lighting or reflections
- Lip movements that don’t match the audio
- Slight robotic pauses or unnatural eye contact
- Sudden urgent requests involving money or data
Simulated deepfake training sessions can dramatically improve detection instincts.
3. Deploy AI-Powered Detection Tools
Integrate tools like Reality Defender or FakeCatcher into internal communication systems. For high-risk departments (finance, HR, PR), set up automatic authenticity checks for all incoming video or audio content.
4. Use Digital Signatures and Watermarks
Encourage executives and content creators to embed cryptographic signatures or invisible watermarks in official videos. These act as authenticity stamps that prove the content’s origin.
5. Continuous Monitoring with Threat Intelligence
Advanced security suites such as Splunk, Microsoft Sentinel, and Darktrace can detect anomalies in digital behavior — for instance, suspicious transfers or unusual meeting patterns.
Pair these insights with real-time threat feeds that monitor emerging deepfake scams.
Future of Deepfake Security
The fight between AI creators and AI defenders is escalating into a true arms race.
Here’s what to expect in 2025 and beyond:
- Built-in Verification: Major platforms like Zoom and Google Meet may add authenticity checks by default.
- Legal Frameworks: Governments are drafting deepfake disclosure laws that require labeling synthetic media.
- AI vs AI Detection: New “counter-GANs” will learn to detect fake patterns even from unseen models.
- Biometric Evolution: Advanced liveness detection (eye movement, pulse analysis) will make authentication harder to fool.
- Consumer Tools: Expect mobile apps that quickly scan a video or voice note for deepfake manipulation.
As detection improves, trust online will depend on verified proof, not appearance.
Final Thoughts: Trust, but Verify
Deepfakes mark a turning point in cybersecurity — one where our eyes and ears can no longer be trusted.
The $25 million scam proved that even seasoned professionals can fall victim when realism meets urgency.
To protect yourself and your organization:
- Treat all unexpected video or voice messages with caution.
- Adopt deepfake security tools that validate authenticity in real-time.
- Train your teams continuously.
- Verify identity through multiple secure channels.
- Stay informed as new AI threats evolve.
With awareness, technology, and sound security policies, we can make sure the promise of AI doesn’t become its own biggest danger.
Further Reading & References
- Financial Times – Deepfake Video Call Scam Cost Firm $25 Million
- The Guardian – Hong Kong Company Duped in Deepfake Video Conference
- Intel – FakeCatcher: Real-Time Deepfake Detection Technology
- Reality Defender – Official Deepfake Detection Platform
- Business Insider – AI Voice Cloning and Financial Fraud
- Microsoft Video Authenticator Overview
Recommended Internal Reading
Boost your understanding of cybersecurity, AI threats, and deepfake defenses with these related articles from CyberNet24:
- Top Cybersecurity Tools of 2025 – Learn about the latest tools to strengthen your organizational defenses.
- AI Cybersecurity vs Hackers: The New Battlefield – Explore how AI is used in both offense and defense in modern cybersecurity.
- Cybersecurity Guide for Remote Workers – Essential practices for securing work-from-home environments.
- Importance of Software Updates – How keeping software up-to-date prevents breaches and vulnerabilities.



