Zero Trust: Why “Never Trust, Always Verify” Is the New Standard for Staying Safe

For decades, we treated cybersecurity like a medieval castle. We built high walls and deep moats (firewalls and VPNs), assuming that as long as you were inside the gates, you were one of the “good guys.”
But the world has changed. With the rise of cloud computing, remote work, and coffee-shop Wi-Fi, the “castle” no longer has walls. Today, attackers don’t just break in; they often walk through the front door using stolen credentials. This shift is why Zero Trust Architecture (ZTA) has moved from a buzzword to a necessity. It’s a security model built for the way we actually work today.
What is Zero Trust, Really?
At its heart, Zero Trust is a simple mindset shift: Never trust by default. Always verify.
In a Zero Trust world, being “on the network” doesn’t give you a free pass. It doesn’t matter if you’re sitting in the corporate headquarters or a home office; every single request to access data is treated as a potential risk until proven otherwise. We stop looking at where you are and start looking at who you are, the health of your device, and the context of your request.
Why the “Old Way” Isn’t Cutting It
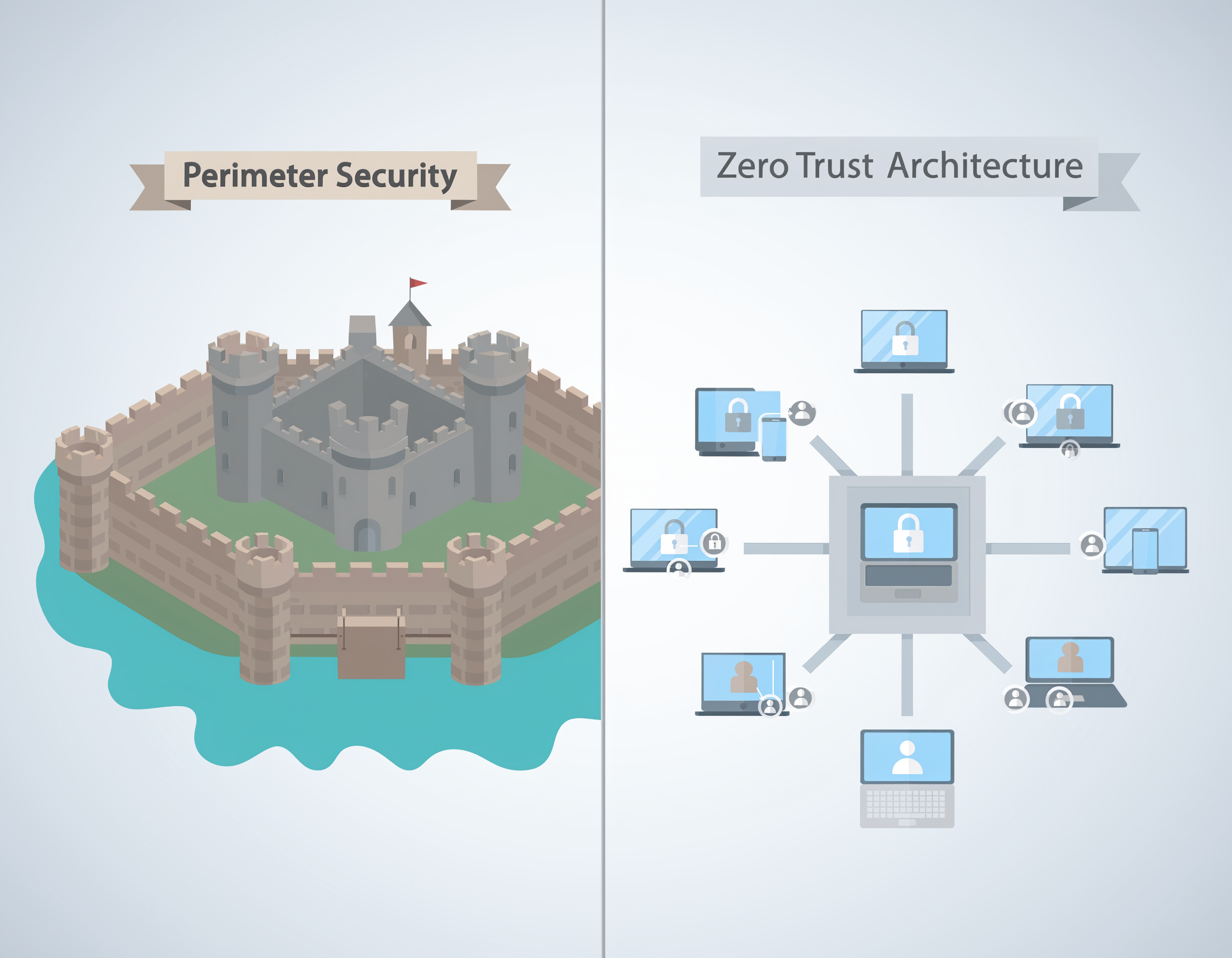
The traditional “perimeter” model is crumbling because our digital lives are no longer contained in one building. Think about it:
- We use personal phones for work.
- Our data lives in third-party SaaS platforms.
- Phishing scams have become incredibly convincing.
- Once an intruder gets past the firewall, they have “lateral” freedom to roam anywhere.
Essentially, our perimeters have become porous, and “blind trust” has become a liability.
The Four Pillars of Zero Trust
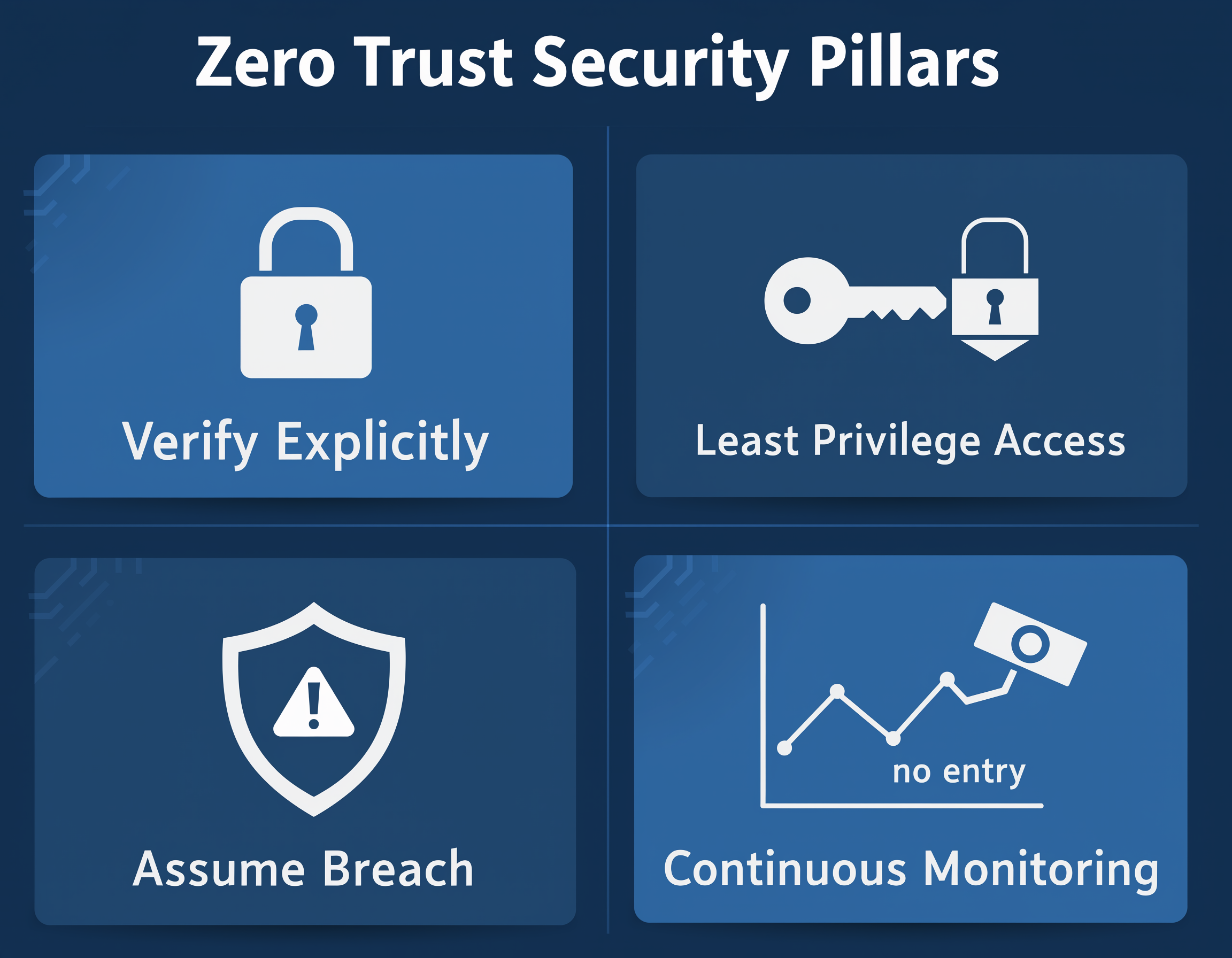
Zero Trust isn’t a piece of software you buy; it’s a strategy built on four core principles:
- Verify Explicitly: Don’t take identity for granted. We use MFA, check the device’s security status, and look at behavioral signals (like “Why is John logging in from overseas at 3 AM?”) every single time.
- Least Privilege Access: This is the “need to know” basis. You get the minimum access required to do your job, for a limited time. If a login is compromised, the damage is contained.
- Assume Breach: We stop playing “defense only” and start operating as if an attacker is already inside. This shifts the focus to containing the fire and stopping “lateral movement.”
- Continuous Monitoring: Security isn’t a one-and-done event. We constantly re-evaluate risk. If your device suddenly shows signs of malware, your access is revoked instantly.
The “Engine Room” of Zero Trust
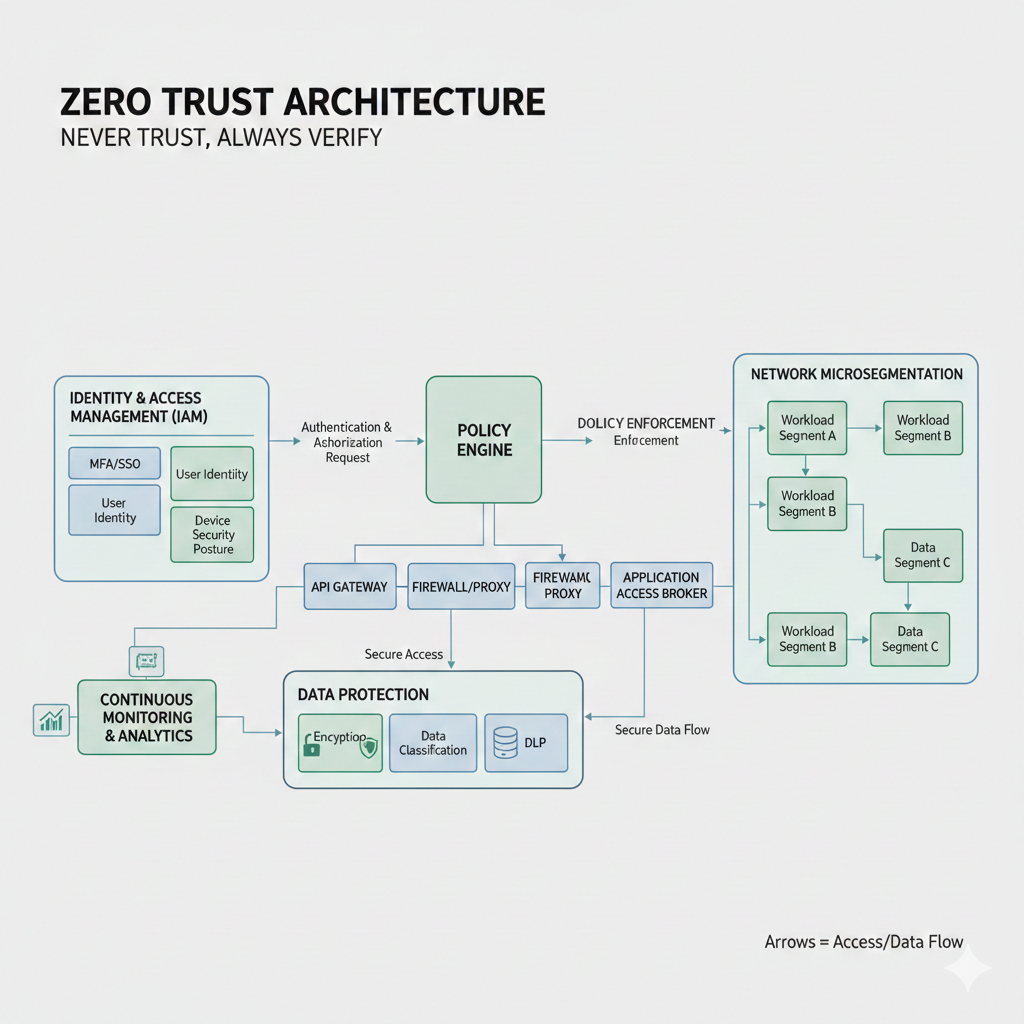
To make this work, several components have to talk to each other:
- Identity (IAM): Identity is the new perimeter. We use tools like MFA, SSO, and OAuth to ensure you are who you say you are. Read more on IAM best practices.
- The Policy Engine: The “brain” of the operation. It weighs the risk of every request (integrating AI for adaptive decisions in 2026).
- Policy Enforcement Points (PEPs): The “bouncers” at the door—gateways and firewalls like Zscaler ZTNA that execute the brain’s decisions. Zscaler implementation example.
- Microsegmentation: Instead of one big room, we divide the network into small, secure zones. Even if a thief gets into one room, the others stay locked.
- Data Protection: We protect the “crown jewels” themselves through encryption, DLP, and quantum-resistant crypto for future threats.
Real-World Success Stories
Zero Trust delivers results. A global bank implemented micro-segmentation and saw security incidents drop 40% in the first year. Healthcare providers using IAM and continuous monitoring reduced unauthorized access by 60%, boosting HIPAA compliance. Small businesses via tools like AWS IAM report faster threat detection without massive overhauls. More Zscaler success stories.
Industry Benchmarks
If you’re looking for a roadmap, most experts point to the NIST SP 800-207 standard (PDF)—the gold standard for data flows and policy-driven access. You’ll also see frameworks from Gartner ZTX and the CISA Zero Trust Maturity Model to assess your progress visually.
Facing the Reality: It’s a Journey, Not a Switch
Switching to Zero Trust isn’t easy. It’s a marathon, not a sprint. Organizations often run into:
- Ancient “legacy” systems that don’t play well with modern identity tools (solve with API gateways).
- The complexity of writing new security policies (unify via dashboards).
- A bit of “change fatigue” from employees (automate to reduce friction).
- Costs (phase rollouts starting with high-value assets).
5 Actionable Steps to Start:
- Assess assets and prioritize critical data.
- Roll out MFA everywhere.
- Implement just-in-time access and PAM.
- Add micro-segmentation for legacy systems.
- Set up dashboards for real-time monitoring. AWS Zero Trust roadmap.
The Bottom Line

Zero Trust isn’t about being cynical or “distrusting” your employees. It’s about resilience. In 2026, with AI threats rising, it’s how modern organizations survive breaches without catastrophe. Start small—your firewalls are a great foundation.
Related Articles
If you want to explore more professional cybersecurity guidance, the following trusted resources may be helpful:
- The importance of software updates: Why installing patches protects you
- Cybersecurity for remote workers: How to secure your home office network
- How to choose a VPN: Beginner’s guide to secure online privacy
- Top Cybersecurity Tools 2025 — Reviews & clear recommendations
- Networking tips for beginners: A complete guide (2025)
- AI vs hackers: How artificial intelligence is transforming cybersecurity


